IT Security
Cybercrime needs to be stopped in a way that fits the needs of your business. Our professionals make sure hackers don’t get in by coming up with proactive IT security service plans.

Overview
The Cyber Security vertical is dedicated to supporting enterprises – both in the public and the private sectors – and the Government, to secure their information assets and information infrastructure in a smart and proactive way with particular emphasis on capacity building through thought leadership.
Our Security Experts offer a holistic approach to your security needs addressing all aspects of your IT infrastructure.
Our Security Solutions include Firewalls, UTM(Unified Threat Management), Security Assessment including policy compliances, Web content filtering, Log management, Anti- Phishing, Posture Validation, VAPT (Vulnerability Assessment and Penetration Testing), Proactive monitoring of internal and external threats including remote monitoring.
Computer crimes, frauds, Corporate espionage, disgruntled employees and trigger-free hackers have led to astronomical losses to companies of all sizes throughout the globe.
Did You Know
global cybercrime damages predicted to cost $6 trillion annually by 2021
Source : cybersecurityventures
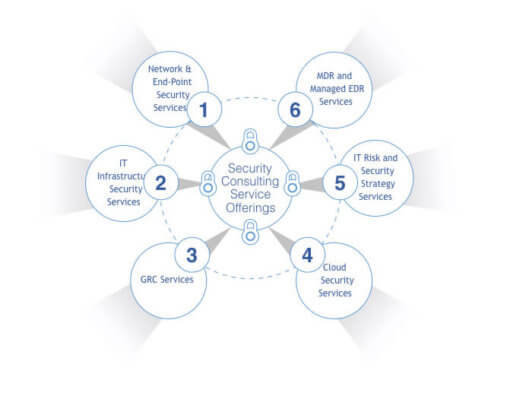
Our Services
IT Risk and Security Strategy
- Program Assessment
- Framework Integration
- Policy Development
- Vulnerability Management Program Design and Implementation
- Mobile and Cloud Security Strategy
- Security Program Development
- IT Risk Advisory Services
Application Security
- Application Assessment
- Architecture Design Assessment
- Threat Modeling
- Secure Software Development Lifecycle Assessment
- Product Security Assessment
Mobile Security
- Mobile Application Assessments
- BYOD Strategy & Policy
- Mobile Security Framework Maturity Assessment
- Secure Mobile Architecture Review
- Mobile Device Forensics
- Multi-Network Stack Assessment
- Firmware/OS Code Review
Cloud Strategy
- Rapid Secure Cloud Application Deployment
- Cloud Application Assessments
- Cloud Data Compliance
- Cloud Infrastructure Assessment
Compliance Services
- PCI Readiness Assessment
- ISO 27001 / 27002 deployment and Assessment
- Enterprise Risk Assessment as per ISO 31000
- HIPAA / HITECH
- NERC CIP
- DIACAP
- MA & NV State Data Protection Standards
Infrastructure Security
- Network Architecture Assessment
- Network and Endpoint Vulnerability Assessments
- Penetration Testing
- IT Infrastructure Profiling and Assessment
- Firewall / IPS/IDS Deployment and Management
- Anti APT Solutions
- Network Traffic Behavior Analysis
Cyber security statistics 2019
Is Your Company At Risk
Of companies have over 1000 stale
Not protected including credit card
The threats.They’re seeing can be blocked by their anti-virus software.
Services Details
A. Network and End-Point Security Services
Infrastructure Security services help organizations:
- Understand the true boundaries of the extended enterprise, including overall risk to critical assets
- Ensure comprehensive infrastructure security
- Validate the effectiveness of existing network and endpoint controls against industry and company standards
- Develop the ability to prevent, detect, and respond to attacks
- Identify and mitigate the most common threats to the infrastructure and its components
Network Security Services Include

Network Architecture Assessment :
Our Network Architecture assessments provide an in-depth and structured technical assessment against secured design practices, operational requirements, and system risk profiles.

Network and Endpoint Vulnerability Assessments :
Assessments of network and endpoint security utilize a combination of automated network-based scans and root cause analysis to develop a snapshot of your network and endpoint security posture.

Penetration Testing :
Mature Penetration Testing service includes an active analysis of network vulnerabilities and simulation of attacks exploring both known and unknown hardware or software flaws, as well as, operational weaknesses in either process or technical countermeasures.

IT Infrastructure Profiling, Posturing and Assessment :
Survey and development of in-depth knowledge about what’s in your ecosystem to enable key stakeholders to make decisions based on how the environment is configured, rather than the desired state
B. IT Infrastructure Security Consul/Ng Services
According to some experts, blockchain has the potential to completely transform the information technology industry as we know it. Transactions can be completed in a way that is resistant to fraud, trusted, and secure thanks to the use of blockchain technology. It was designed to make trading in the digital currency Bitcoin more convenient. It eliminates the need for intermediary organizations such as financial institutions, banks, and other similar organizations, in addition to preventing the alteration or modification of data within these blocks. A managed blockchain has the potential to completely transform the way businesses are run because it can store transactions in a more secure and reliable manner.
Advisory services
Advisory services
- IT risk management and governance
- Network and Security Segmentation
- Cloud Security Advisory
- End-Point Detection and Response (EDR) Advisory
- Security Operation Center Advisory
- Managed Detection and Response Advisory
Security Strategy and Framework Development Services
Security Strategy and Framework Development Services
- Program Assessment
- Framework Integration
- Policy Development
- Vulnerability Management Program Design and Implementation
- Mobile and Cloud Security Strategy
Assessment services
Assessment Services
- Web Application Security Assessment
- Vulnerability Assessment of Network, Mobile devices, hosted environment / cloud
- Code review and secure coding
- Digital Forensics
C. GRC Services
- ISO 27001: 2013 – ISO 27001 advisory services to support readiness prior to certification – ISO 22301 advisory and readiness prior to certification
- PCI-DSS – Performs readiness assessments on payment applications according to the Security Procedure and the PA-QSA Validation Requirements.
- Implementation, Gap assessment and compliance of ISO 27001 (Information Security), ISO 22301 (Business Continuity), ISO 20000 (IT Service Management), PCI DSS, SOC II, etc
- GDPR Compliance
- Compliance of regulatory requirements (Indian Context) in financial domain with Govt mandates released from RBI, ReBIT, IDRBT
- Compliance of regulatory compliance (Indian context) in insurance domain as per IRDA
- Compliance of regulatory compliance (Indian context) in power & energy domain as per NCIIPC
- Consulting for CERT In empanelment
- BYOD control consulting
D. Cloud Security Services
Cloud Data Compliance
Cloud data compliance services are flexibly designed to address the complex challenges of maintaining regulatory compliance when leveraging public or private clouds as part of a regulated environment. Virtualized infrastructures present a challenge in understanding the full extent of data protection and privacy issues. Cross-geographic deployments of infrastructure may violate regulatory requirements in public clouds. Effective policy development and the appropriate level of controls and configuration of services are key. Any or all of these issues can be addressed via advisory services focused on Cloud Data Compliance.
Cloud Infrastructure Assessment
Whether assessing a public or private cloud environment, this assessment is built on the foundation of the enterprise infrastructure security assessment methodology that has used for years and layers on concerns specific to cloud-based computing. The scope is flexible depending on the situation and typically includes the storage, compute and service layers of the cloud stack. As with all cloud- related services, data protection is a core component anywhere that critical applications and data will reside.
E. IT Risk and Security Strategy Services
Program Assessment – Our Program Assessment service allows us to assess and report on the state of the organization’s security program, including analysis of people skills, process and methodologies, policy completeness and effectiveness, usage of tools, and finally, what metrics are measured and how they are reported.
Framework Integration – Our Framework integration services assist clients in aligning security frameworks with industry standards, such as ISO 27001 and 27002, NIST 800-53, COBIT and ITIL.
Policy Development – Help clients to develop security policies that align security requirements with business requirements, taking into account people, technology and process.
Vulnerability Management Program Design and Implementation – Expert in developing methodology and process to actively detect, prioritize, and remediate vulnerabilities against evolving threats.
Mobile and Cloud Security Strategy – As a core focus area, Mobile and Cloud Security Strategy services help clients assess, develop and integrate the security policies and controls governing the use of mobile and cloud computing products and services.
F. MDR and Manage EDR Services
Our Managed detection and response (MDR) service provides 24/7 threat monitoring, detection and lightweight response services to customers leveraging a combination of technologies deployed at the host and network layers, advanced analytics, threat intelligence, and human expertise in incident investigation and response. Our approach is to undertake incident validation, and offer remote response services, such as threat containment, and support in bringing a customer’s environment back to some form of “known good.”
As per Industry report, by 2020, 15% of organizations will be using MDR services, up from less than 5% today. Demand from midsize enterprises has been particularly strong, as MDR services are viewed as a better fit than procuring security event monitoring services from an MSSP.
Our core strength is our People and the entire MDR service right from its inception to architecture, design, plan, implementation and operation is meticulously executed by this passionate team. Our deep understanding of cyber security domain has helped us carefully design MDR services which is agile, fit for different types of consumption model and address tomorrow’s security challenges.
Our MDR and Managed EDR service has both Cloud as well as on-prem model where customers can select services like End-point management, DNS protection, Anti-Phishing, and monitor Netflow traffic both East-West and North-South traffic.